Think this computer is rooted?
I've got somebody's very infected Windows 7 laptop I'm working on. In Safe Mode, everything works normally, but in normal operation with all startup programs unchecked and all non-Microsoft services unchecked in msconfig, I am getting errors about DLLs at the login screen and whenever things are clicked on the desktop or start menu. It seems as if the virus put code in some critical libraries and is executing it often. I used MalwareBytes to clean the machine (which wouldn't even boot prior to that except into Safe Mode) and now these errors plague it.
I'm probably going to nuke it and reinstall Windows tomorrow night, unless anyone has any tips or suggestions for fixing these errors. I have already run "sfc /scannow" after running MalwareBytes. System Restore returns the computer to an infected state.
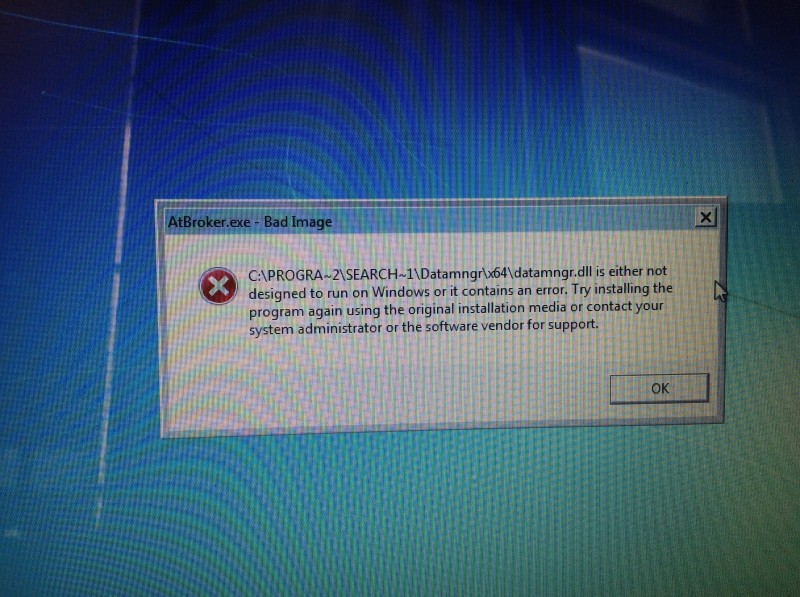
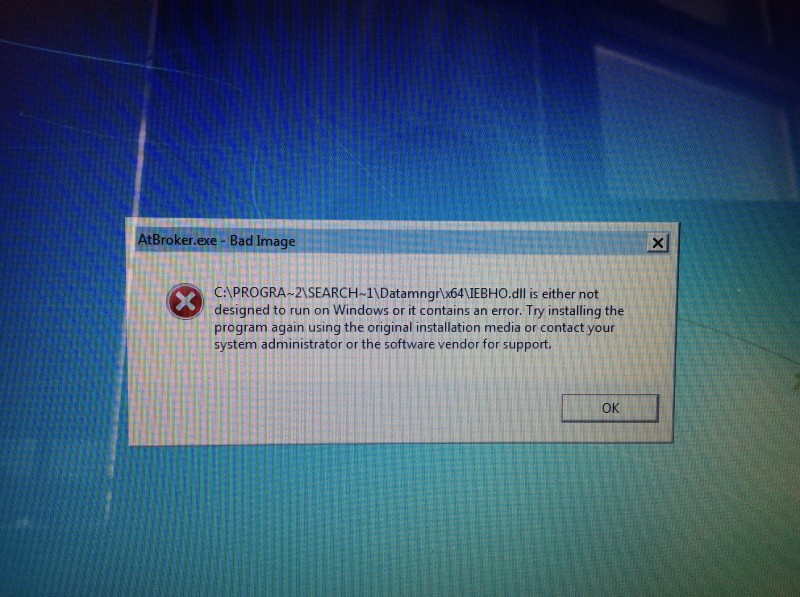
I'm probably going to nuke it and reinstall Windows tomorrow night, unless anyone has any tips or suggestions for fixing these errors. I have already run "sfc /scannow" after running MalwareBytes. System Restore returns the computer to an infected state.


Comments
That's the Windows Assistive Technology executable (I think this is Ease of Access, unsure). How or why would failware attack Ease of Access? That's just dumb.
Nevertheless, try copying original versions of these .dlls in those errors to their places and see what happens.
What I don't understand is why x64 libraries are in the x86 Program Files folder.
I'm sure there's something somewhere on this.
Easy. It runs with elevated privileges. Pretty common attack / prank is to replace the ease of access executable with cmd.exe to allow you to launch an elevated command prompt. From there, you can pretty much do whatever you want with the system.
They could possibly be using the Appinit_dlls sections in the registry to hook into every program's launch so check there too.
This should be completely salvageable, unless you really want to blow windows away and install 150 updates again.
It also runs off of winlogin to provide assistive technology for entering your user/password. In this method it runs under NT_AUTHORITY or some other highly privileged account.
Kirk: Grab a hirens disc and run ESET online or some shit. You will have far better luck when you're not working with the actual infected OS.